[More] Fun with WCF, SharePoint and Kerberos
This is a follow up to the post Fun with WCF, SharePoint and Kerberos – well it looks like fun with hindsight
When I wrote the last post I thought I had our WCF Kerberos issues sorted, I was wrong. I had not checked what happened when I tried to access the webpart from outside our TMG firewall. When I did this I was back with the error that I had no security token. To sort this we had to make some more changes.
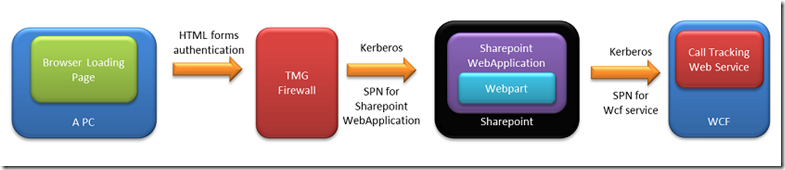
This is the architecture we ended with.
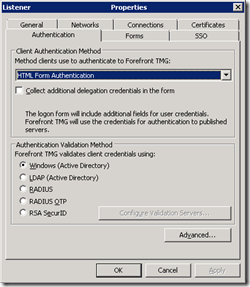
The problem was that the Sharepoint access rule used a listener in TMG that was setup to HTML form authentication against our AD
and the rule then tried to authenticate our Sharepoint server via Kerberos using the negotiated setting in the rule. This worked for accessing the Sharepoint site itself but the second hop to the WCF service failed. This was due to use transitioning between authentication methods.
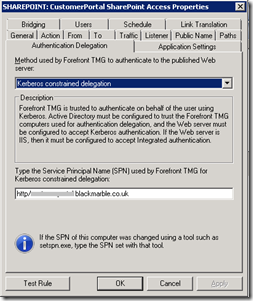
The solution was to change the access rule to Constrained Kerberos (still with the same Sharepoint server web application SPN)
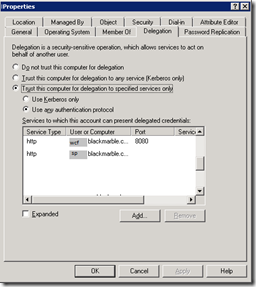
The TMG gateway computer (in the AD) then needed to be set to allow delegation. In my previous post we had just set up any machines requiring delegation to ‘Trust this computer for delegation to any service’. This did not work this time as we had forms authentication in the mix. We had to use ‘Trust this computer for delegation to specific services only’ AND ‘use any authentication protocol’. We then added the server hosting the WCF web service and the Sharepoint front end into the list of services that could be delegated too
So now we had it so that the firewall could delegate to the Sharepoint server SPN, but this was the wrong SPN for the webpart to use when trying to talk to the WCF web service. To address this final problem I had to specifically set the SPN in the programmatic creation of the WCF endpoint
1this.callServiceClient = new CallService.CallsServiceClient(
callServiceBinding,
1 new EndpointAddress(new Uri("http://mywcfbox:8080/CallsService.svc"), EndpointIdentity.CreateSpnIdentity("http/mywcfbox:8080")));
2```
3
4By doing this a different SPN is used to connect to the WCF web service (from inside the webpart hosted in Sharepoint) to the one used by the firewall to connect to the Sharepoint server itself.
5
6Simple isn’t it! The key is that you never authenticated with the firewall using Kerberos, so it could not delegate what it did not have.